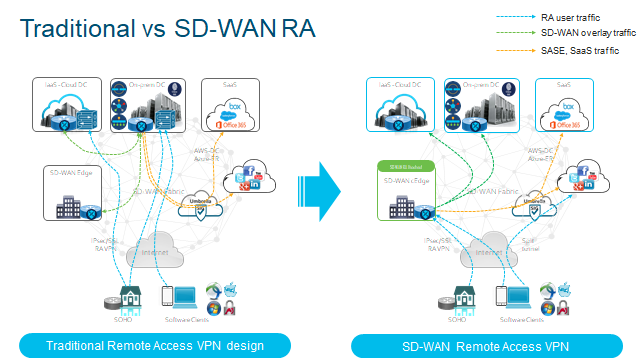
Traditionally, RA will tunnel through one Security Edge Device at the perimeter. Typically this provides challenges such as:
- Deploying SD-WAN means RA will be treated as a separate network.
- VPN hardware may cost more with more users using the service.
- Separate Management Plane.
- Separate policies for RA and Corporate users.
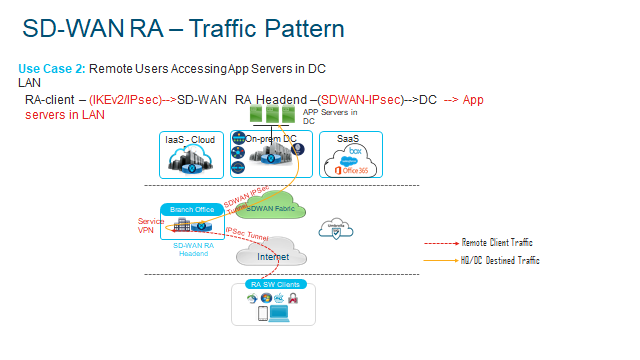
- Traffic traverses through DC which can lead to poor Application Experience.
- Traditional RA is stiched to SD-WAN network at the DC today.
SD-WAN Remote Access Overview
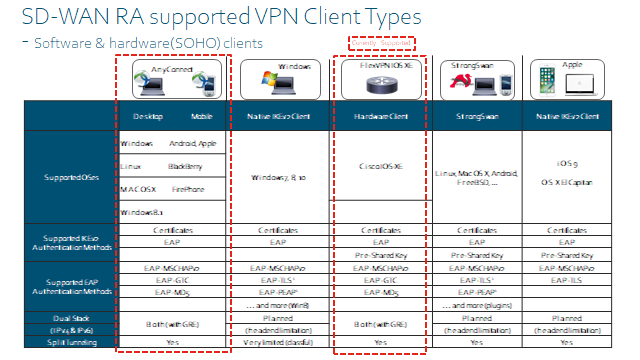
Cisco RA uses FlexVPN, FlexVPN is another method to configure VPN but in a much simpler manner. If you have configured DMVPN Phase 3, you will realise how much configuration is required. FleVPN simplifies this and uses IKEv2.
You deploy a headend device (Router) at the head end network such as where all your applications or services will be ideally.
- IOS-XE supports FlexVPN(IKEv2/IPSec)
- SSLVPN
- As of v20.12 SSL VPN is now supported.
- IOS-XE SD-WAN devices can support RA Headend device.
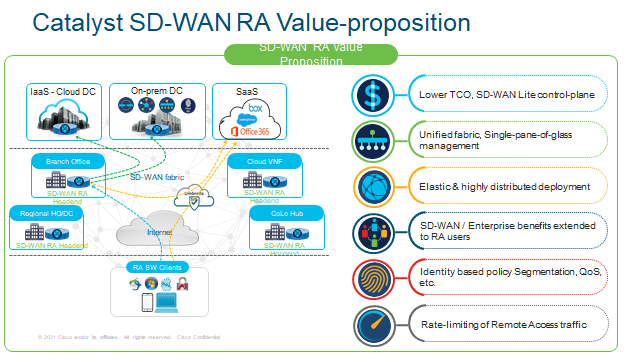
Just going to throw the Sales Pitch into why you would want to use RA!
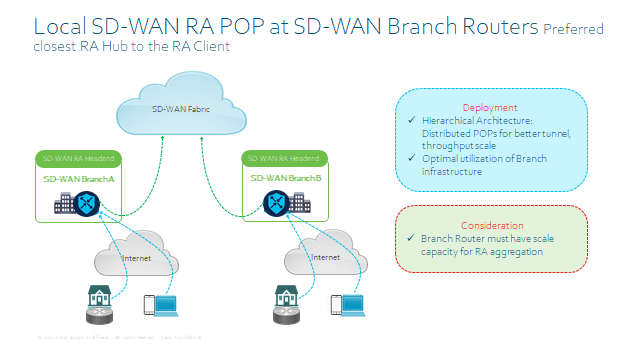
SD-WAN RA – Deployment Considerations
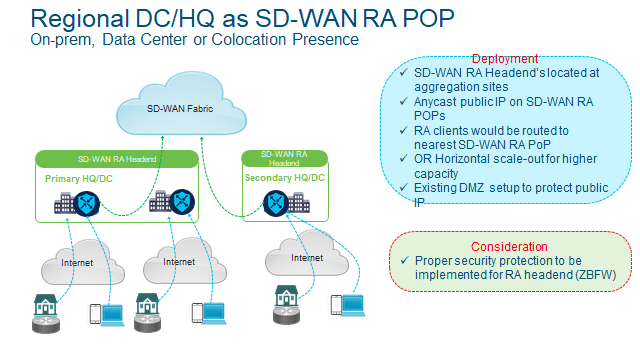
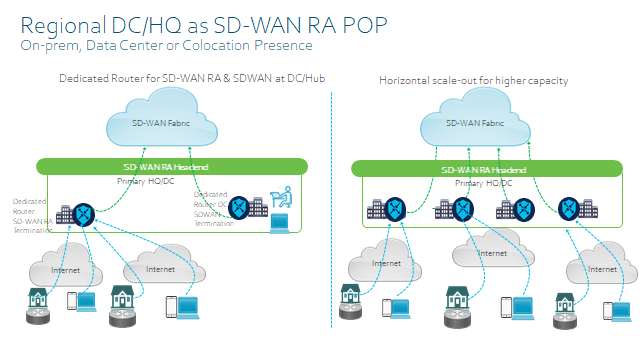
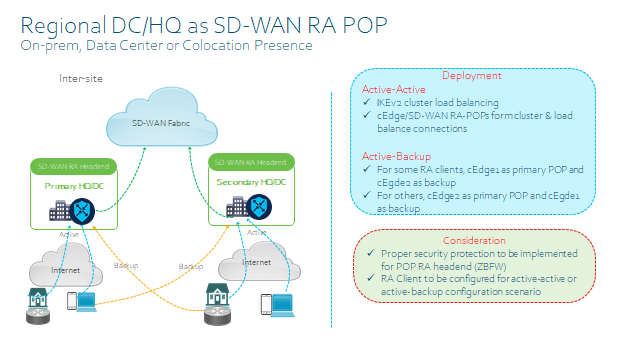
- Static IP on the SD-WAN RA Headend for inbound RA VPN connections.
- Dedicated non-TLOC WAN interface for RA, for Geo-load balancing and also you can configure inbound ACL to restrict traffic to IKEv2 and IPsec as well as now SSLVPN.
- Shared TLOC interface with static public IP
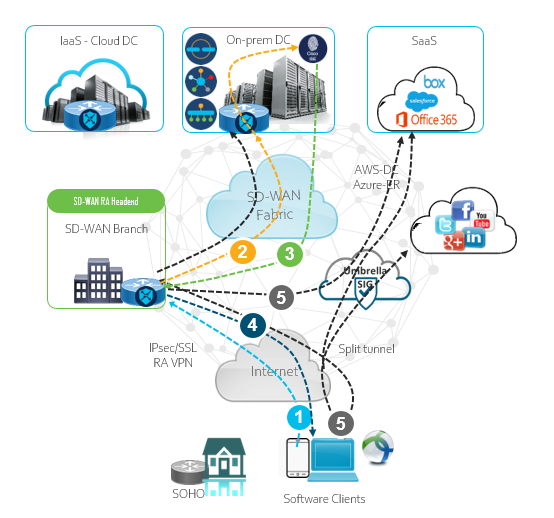
SD-WAN RA – Workflow
- 1 Remote user connects to teh RA headend and requests a IPec/SSL VPN connection
- 2 RA Headend authenticates clients with a certificate or PSK.
- 3 User/Group policy determines the level of access and Client/Subnet is pushed out.
- 4 IPSec virtual interface (per RA user) is created and pushes the IP addresss and DNS etc
- 5 Full or split tunnel routes traffic to the allowed subnets based on the policy set.
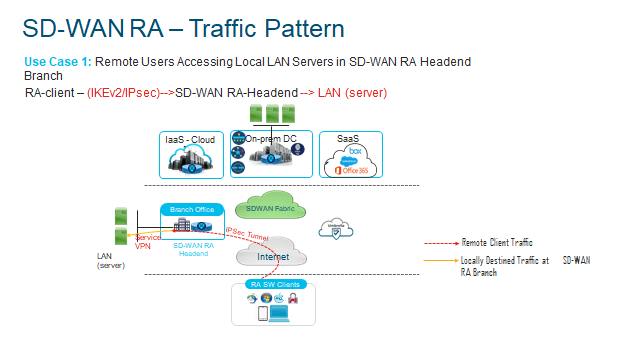
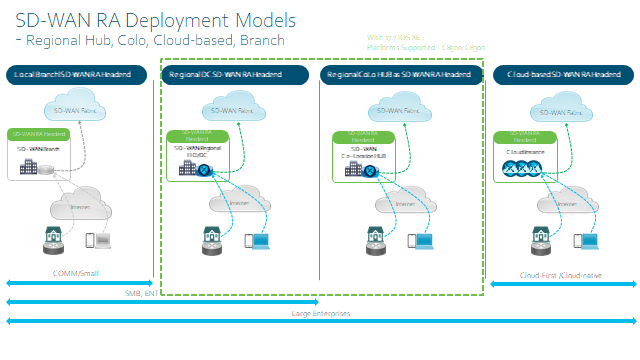
SD-WAN RA Deployment Models
Platform Support
Final thing to consider is the design when implementing RA, is the Headebd device – remember it will need to serve the Service side as well as the usual NAT/DIA sessions on top of the SD-WAN overlay Control Plane as well as Data Plane. So it is best to size appropriately so the box doesn’t set fire to itself!