Before I begin to explain and go through what Cisco Umbrella is I’d like to briefly explain what SASE is so this helps to understand the need and why Cisco Umbrella.
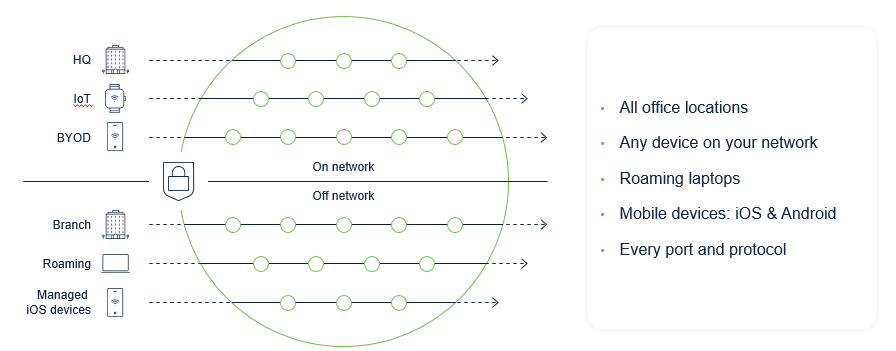
SASE is a different type of achitecture that brings Networking and Security servives as one solution. Designed for strong security from edge to edge, this includes DC’s, branches, remote workers etc.
DNS Security
The first line of defence with Cisco Umbrella is DNS security. You essentially point your DNS to Cisco’s Umbrella DNS server: 208.67.222.222. DNS Security provide the follwing :
- Blocks domains associate with malware, phishing, command and control callbacks anywhere. (C&C servers are used by cybercriminals to send commands to systems compromised by malware and received stolen information from the target network)
- Stops threats a the earliest opportunities as well as malware if it is part of the URL/website.
Cisco Umbrella uses different types of models to track any potential harm/threat.
- Co-occurance model – Identifies other domains that is looked up in rapid succession of a given domain. An example is when a specific domain that is malicious also has other domains tied/looked up with the malicious domain. In essense domain guilty by intereference.
- Natural Language processing model – domain names that spoof terms and brands.
- Spike rank model – detects domains with an unual high spike of traffic.
- Predictive IP space monitoring – Analyses how servers are hosted to detect future malicious domains.
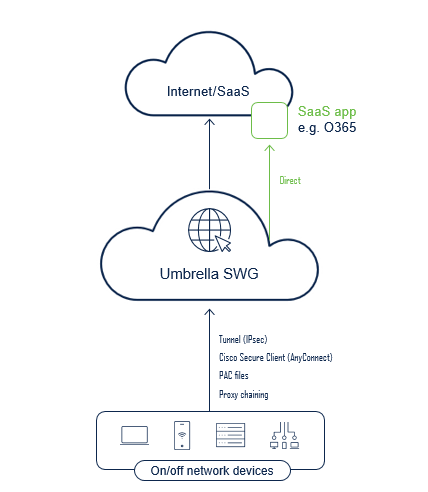
Secure Web Gateway
SWG allows the user to protect the following:
- Anti-Virus and AMP Malware scanning (Advance Malware Protection) – Scan and detect a broad range of malware and viruses which avoids infection and stops any attacks. AMP is another anti virus product for end points. Working together to make sure enterprises are secure twice.
- File Type controls – Prevents downloads of specific files, .exe files etc, also provides visibility of file types.
- SSL decryption – Decrypt HTTS traffic, without HTTPS decryption, you will not be able to see the URL.
- Category and URL filtering for Content control – Content categories is used for ‘acceptable use policies’ for enterprises. You can filter based categories such as ‘adult, Alcohol, News etc’. SWQuses Cisco’s Talos category which is the biggest security group for online activity.
- Threat Grid file sandboxing – Sandboxing is used when there is a new threat that has not been identified/ categorised without much information will be sent to Cisco Umbrella Sandbox in the cloud to be tested and see what is happening.
- App Visibility and control – Can block posts/shares on Social Media, block attachments to webmail apps, and blocks uploads to cloud storage, collaboration, office productivity and content management.
- URL reporting – Visibility for compliance, monitoring and investigations. You can view the URL details by network, user , device and date for : trends, monitor activities and investigate incidents.
Cloud-Delivered Firewall
This is an Outbound firewall, meaning this will only work on the egress side as it leaves Umbrella. If you had other services in a DC or HQ which also have servers and requires users coming inbound to access, Cloud Firewall will not work.
It has the following capabilities:
- L3/L4 Firewall – L7 capabilities
- DPI in NBAR
- IPSec only – When you engage Cloud firewall etc then an IPsec tunnel is setup to Umbrella SIG.
- Multi-geo DC support/location
- Auto failover should primary DC fail – This is done by setting a standby tunnel to another DC using Anycast.
- Firewall logs are exported to AWS S3 bucket.
- An example is SWG blocks MS Web traffic and the fierwall blocks it Voice/video traffic.
- Order of operation is also important with the same rule as when you configure ACLs.
How this works……
Enterprises can choose which data center they wish to utilise Umbrella as their exit point, advantage of Umbrella is that you do not need to build backup IPSec tunnels as this is done automatically. So if a data center fails then the IPSec tunnel will automatically move with minimal down time.
When Customers choose Umbrella, Cisco will provide a static Umbrella Egress IP from the range of 146.112.0.0/16 and 155.190.0.0/16. These IPs will be unique to one per customer.
IPSec Capacity
Cisco offers a maximum of 250Mbps in each direction (Up and Down) IMIX, with ongoing development to increase the capacity.
Multiple tunnels can be deployed to support higher capcity
Failing over to secondary as well as a DR tunnel is done automatically should there be a failure to primary and secondary tunnels.
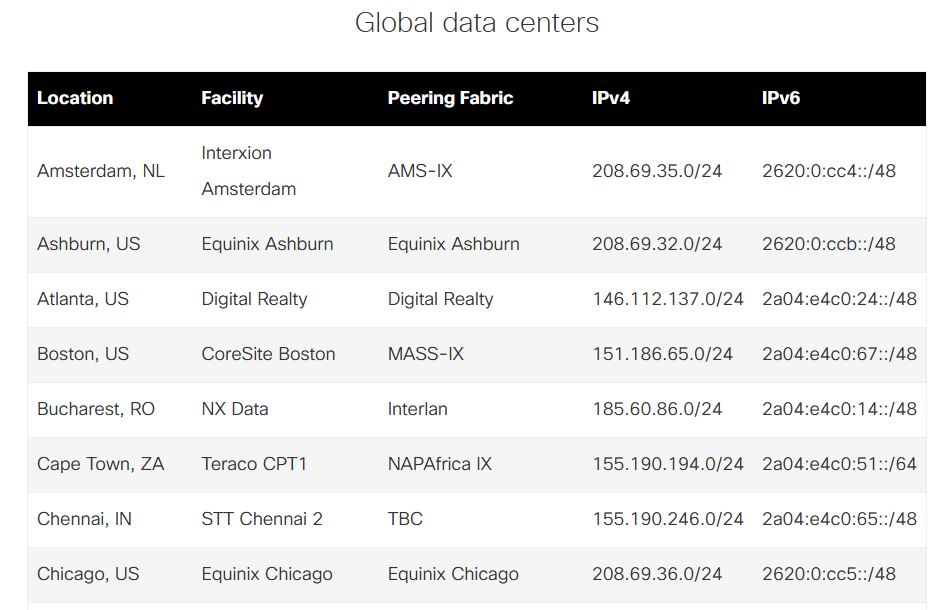
For an up to date list of DCs and regions have a look on the link https://umbrella.cisco.com/why-umbrella/global-network-and-traffic
You will notice that IPv6 is also supported.
CASB – Cloud Access Security Broker
Definition of CASB – Providing a central location for policy and governance concurrently across multiple cloud servises and granular visibility into and control over user activites and sensitive data from both inside and outside the enterprise permieter, including cloud-to-cloud access. What the hell does this actually mean?
Umbrella provides CASB in two ways:
- Inline/Real time which means that traffic to the SaaS provider is intercepted, and scanning/policies are applied before it reaches the SaaS provider.
- Out of band which essentially is SaaS API and this means that when activity goes from the user directly to the SaaS provider then then through an API connection. The CASB applies the policy to provide visibility, protects the user or control their activity.
Cloud malware scans data at rest (Data at rest is data that is not actively moving from device to device or network to network such as data stored on a hard drive, laptop, flash drive, or archived/stored in some other way.) in the SaaS service. Cloud to Cloud scanning
Real Time DLP scans outbound web traffic inline through our secure web gateway proxy for all cloud destinations, whereas SaaS API DLP scans outbound web traffic out-of-band while it’s at rest in the cloud, via restful API, instead of it going through the secure web gateway proxy, but with near real-time enforcement.
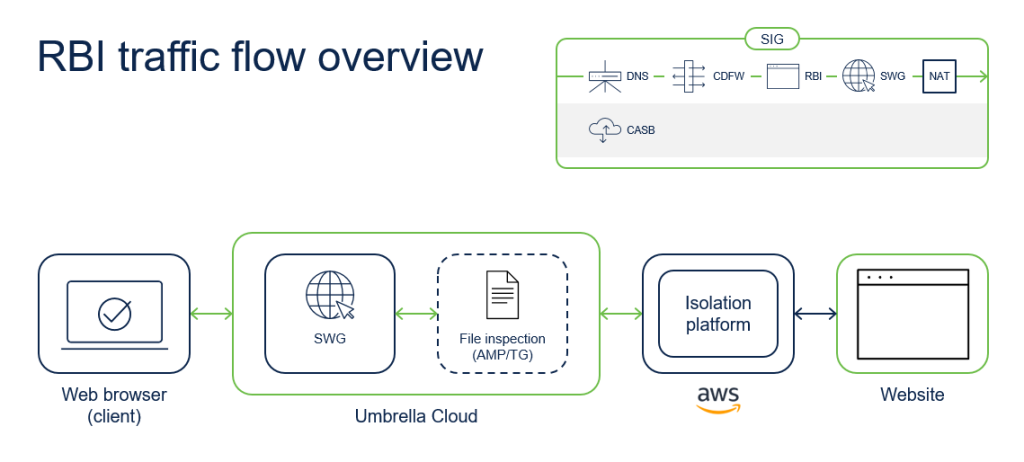
Remote Browser Isolation
Typically if you need to access a potental risky site or uncategorised URL for a legitimate reason, RBI can help. RBI isolates web traffic from the user device and the threat in a air gap enironment. Air gap meaning is the specific device or network is isolated behind closed doors essentially.
RBI frees you from the need to know what’s bad or not. It lets users go where they need, without the risk of malware that hasn’t been detected yet. With RBI, customers can stop browser-based attacks, and users can get a safe browsing experience without sacrificing productivity. IT teams will spend less time dealing with resolving access issues. And since it’s cloud-delivered, RBI is easy to scale on demand, and works with all devices, browsers, and operating systems.
Configuring Basic Umbrella
First of all you would need to change the DNS to Umbrellas DNS – I am using my laptop as an example and pointing the DNS Server
208.67.222.222
208.67.220.220
Then test to make sure it has pointed to Umbrella using the URL https://welcome.umbrella.com/
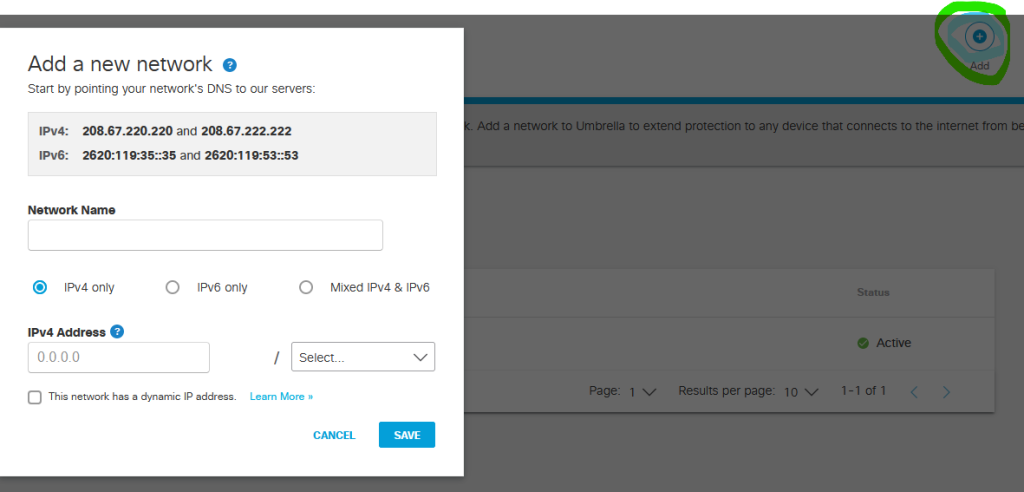
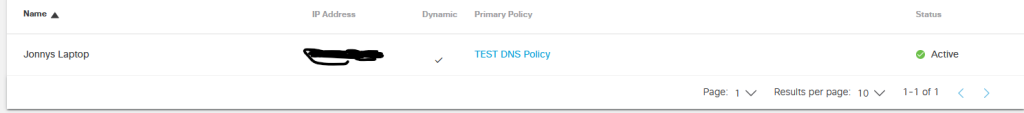
When you login to Cisco Umbrella you will need to create a Network. A Network is what identifies the network or device you are protecting. In this example I chose my laptop which is NAT’d behind a Public Dynamic IP. Now you maybe wondering if it is Dynamic as not every Business may have a Static IP, then how would it work when IPs will change?
With umbrella, you can install a lightweight agent which will continuously poll with umbrella so should there be an IP change it will sync with your Umbrella Network.
Click the add button then you can enter your Public IP and as I can only afford a single IP, I will choose /32.
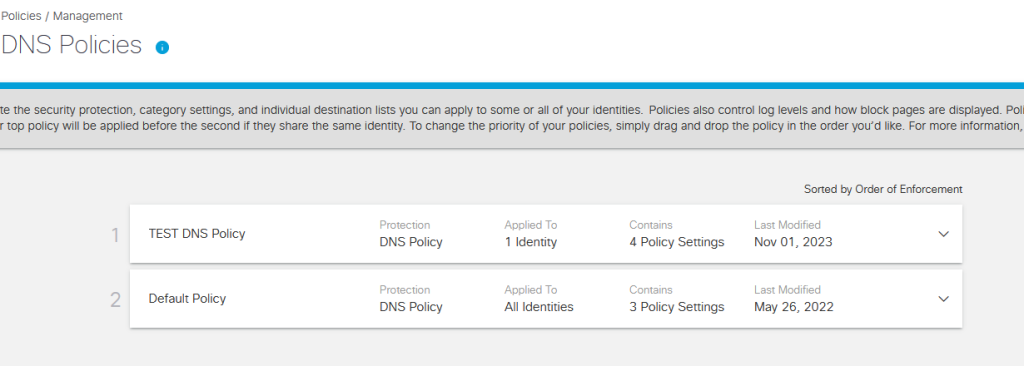
Next, go to DNS Policies
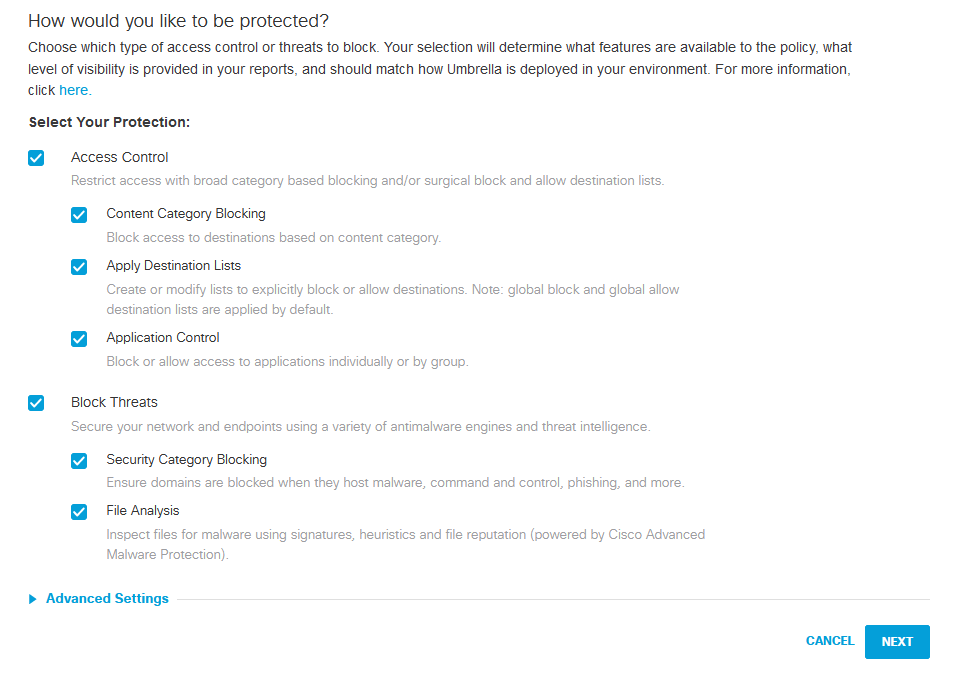
Click to add a new Policy
Click Next
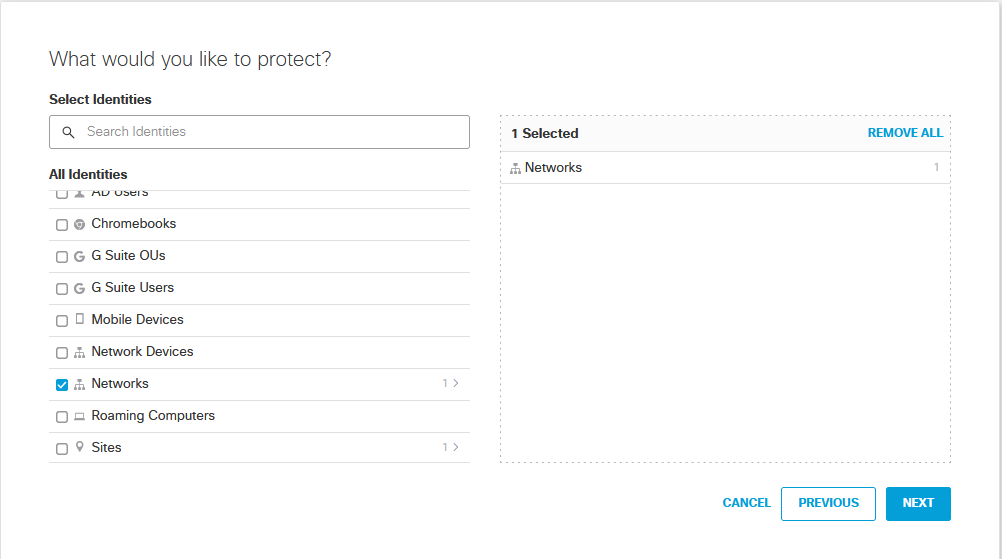
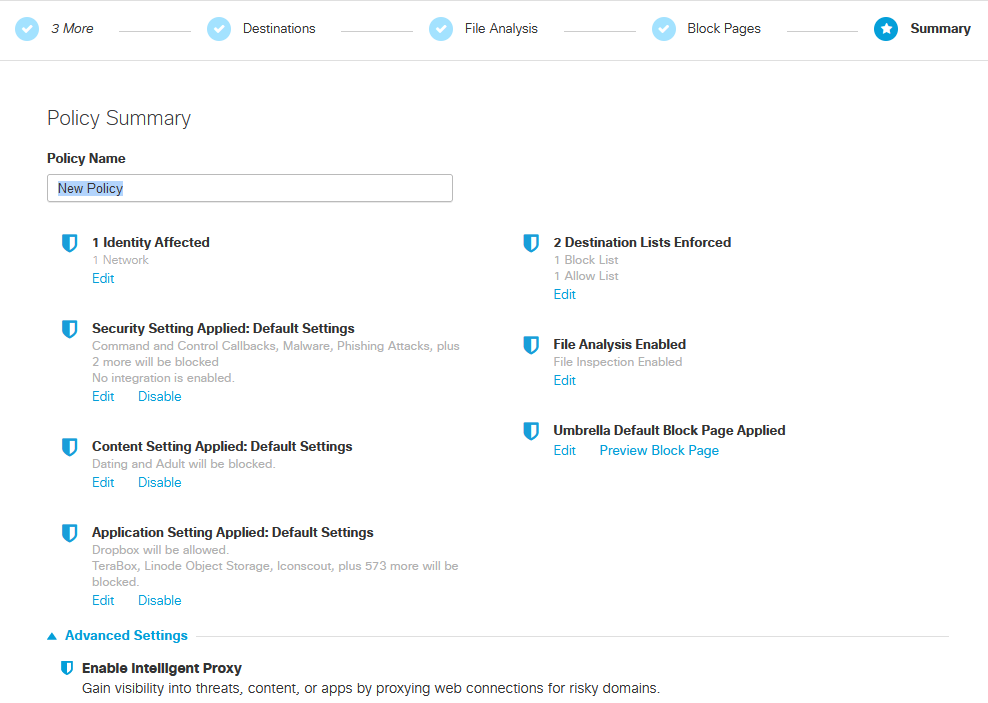
Scroll down until you see Networks, you will notice there is a 1 next to it. Remember on the earlier steps we had to add the Networks which was my laptop I wanted to protect?
Next again
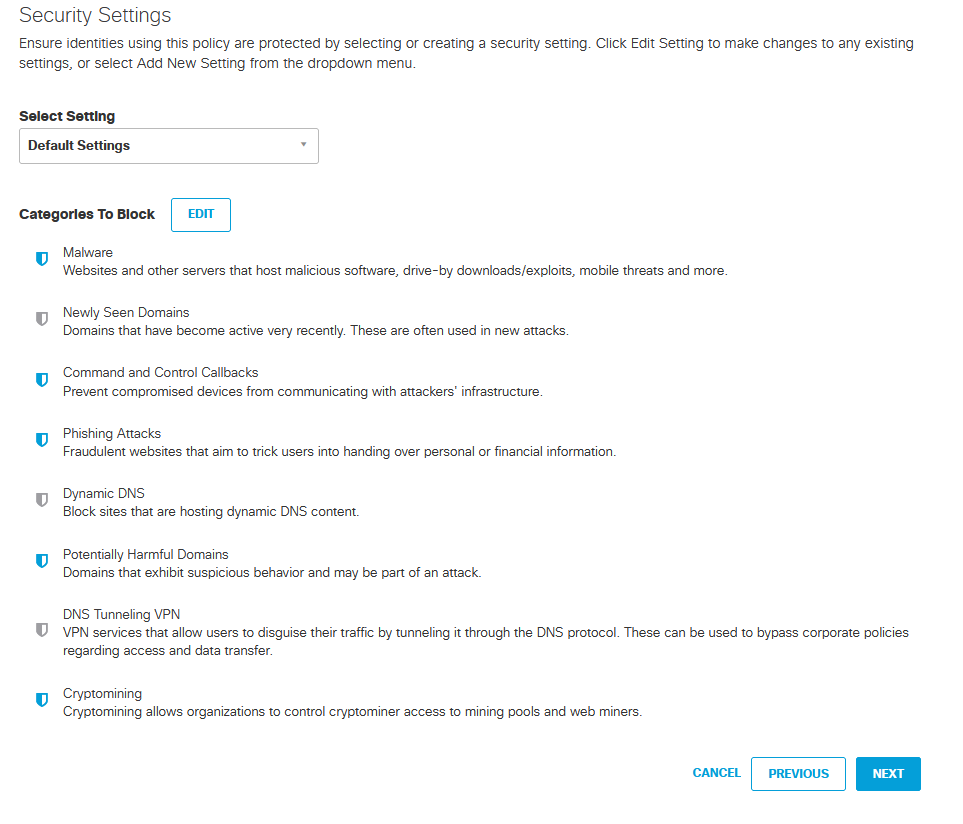
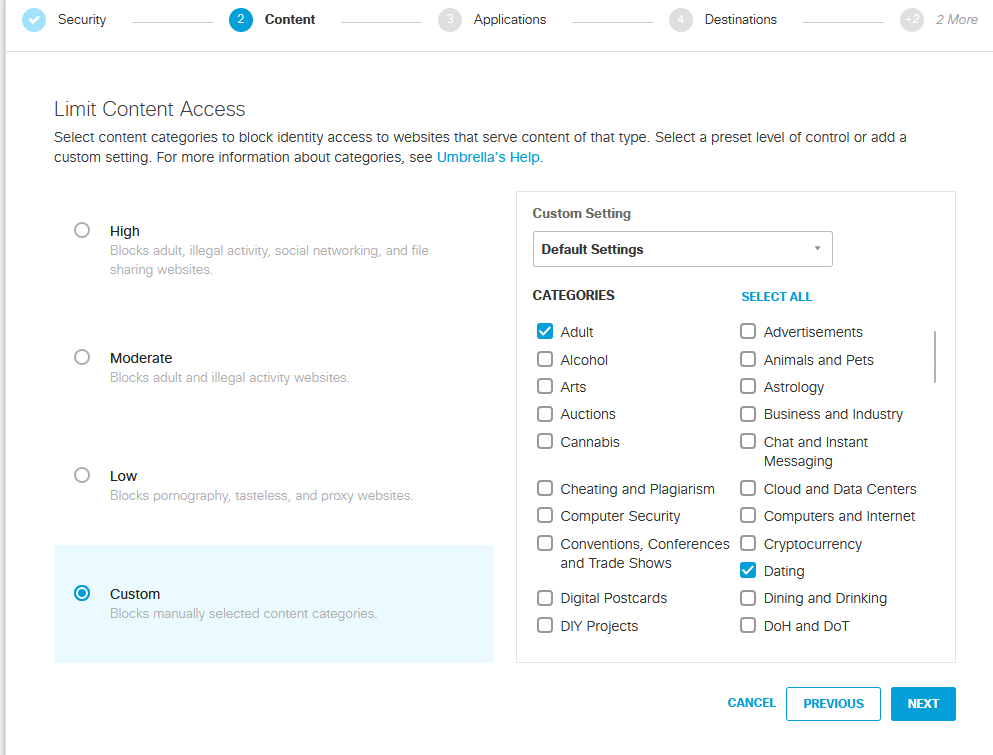
This is where you can block the types of content.
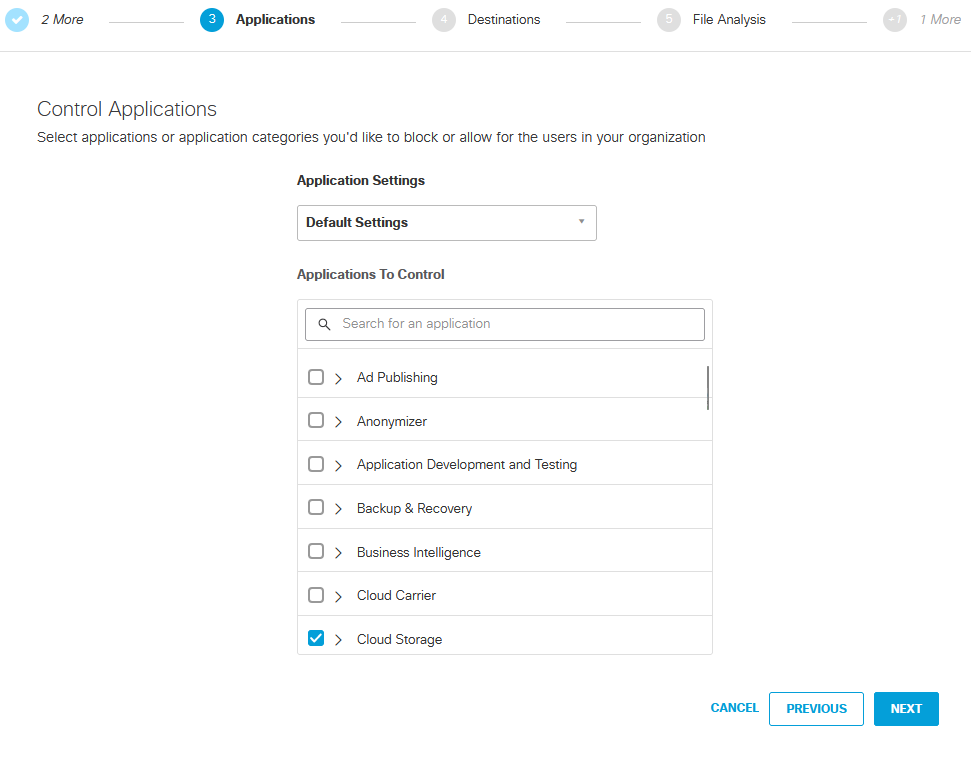
And click next if you do not want to block L7 Applications
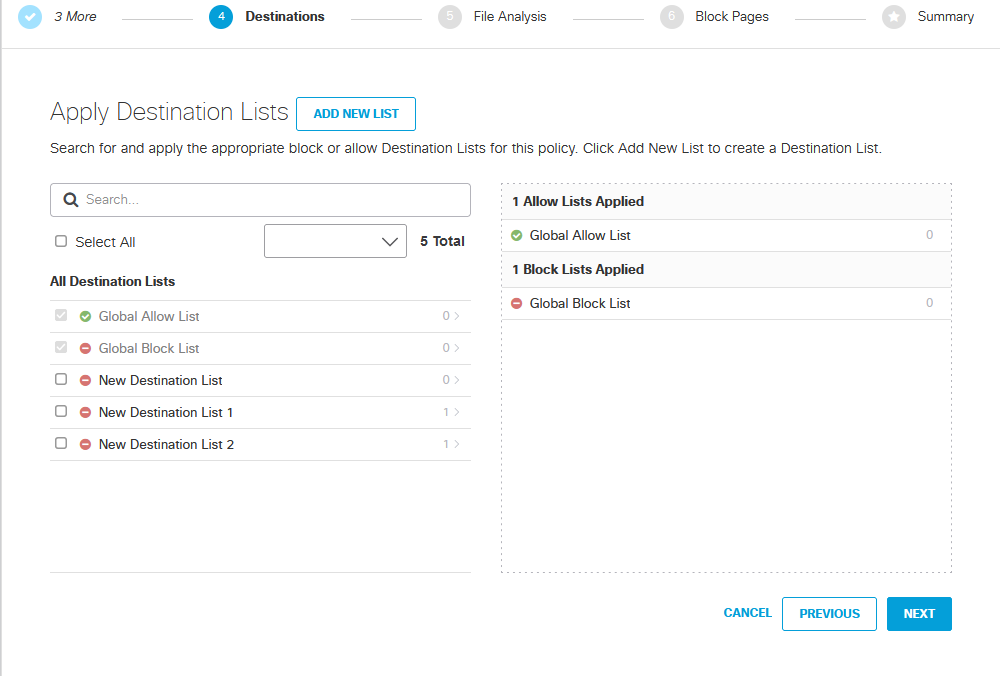
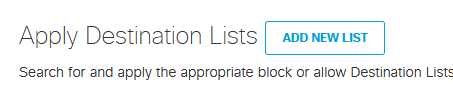
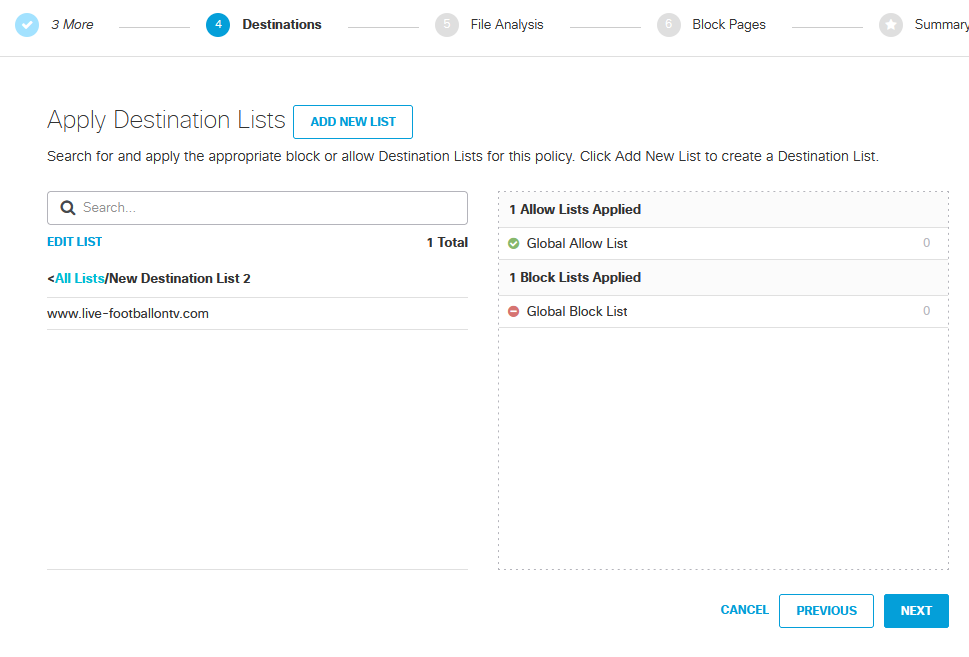
This is where you can block URLs which in this example I will be configuring to block a specific URL.
I have added a new list called New Destination List 2 and it contain the URL www.live-footballontv.com
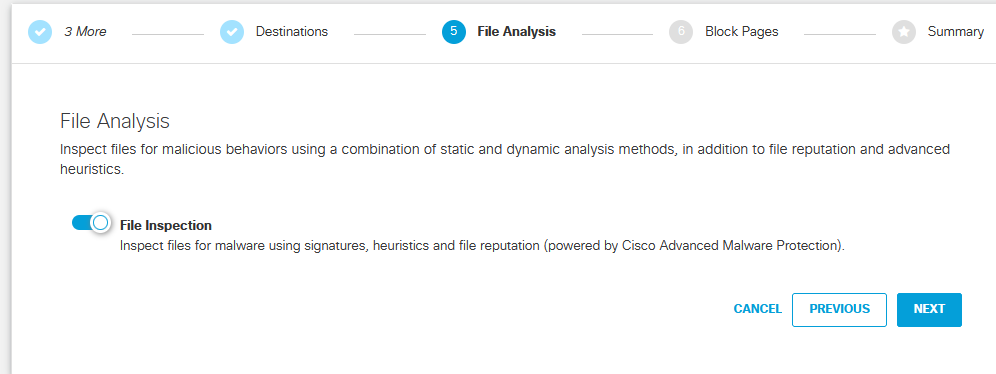
If you wanted file inspection it is on by default then click next.
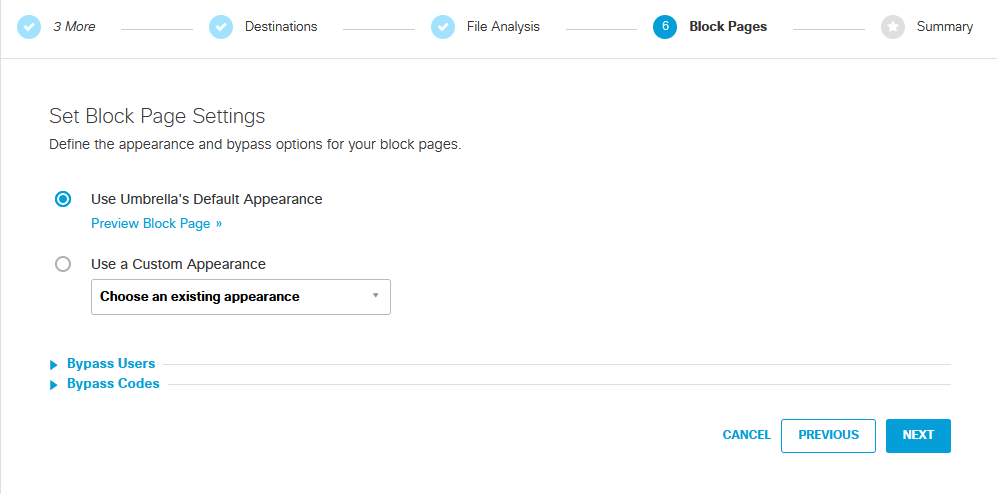
Now, if the end user does access the blocked URL I configured before you can choose which display appearance it provides to the user.
And finally, you can choose to name your new Policy.
As you can see my new Policy is complete. Let’s try the URL I have specifically blocked and see Umbrella work its magic!