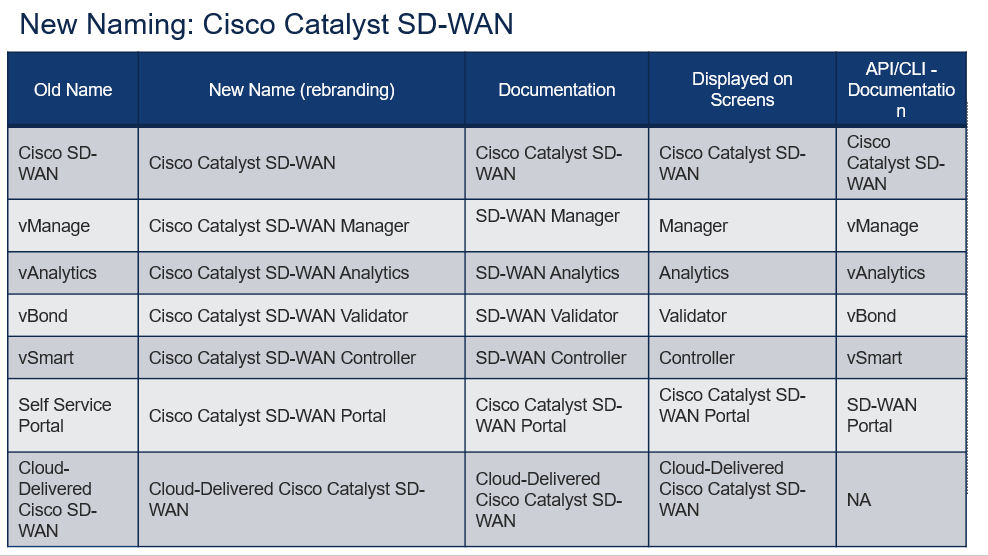
Before I begin explaining what Catalyst SD-WAN is, I’d like to address the new naming for the core components.
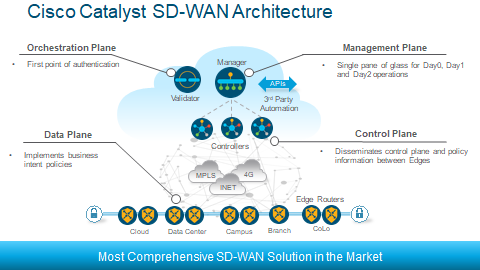
The above is the SD-WAN Architecture.
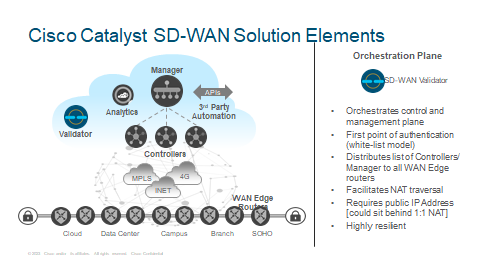
Validator
Cisco Validator is a multitenant part of the Cisco Catalyst SD-WAN fabric. It allows the discovery of the control and management sections of the fabric by leveraging a zero-trust certificate-based white-listed model.
It automatically distributes the list of Controller and the Manager system to the WAN Edge routers during the onboarding process. For situations where Controller, Manager system or the WAN Edge routers themselves are behind NAT, Validator provides the function of NAT traversal, by allowing learning public and private IP addresses.
The discovery of public and private IP addresses allows establishing connectivity across public and private WAN transports. Validator itself should reside in the public IP space or reside on the private IP space with 1:1 NAT.
When delivered as a cloud service, Controller are redundantly hosted in AWS Cloud by default. When deployed as an on-prem solution by the customer, it is the responsibility of the customer to make sure the design allows for resiliency. I have written a post about on-prem SD-WAN below:
http://jaychou.co.uk/?p=618
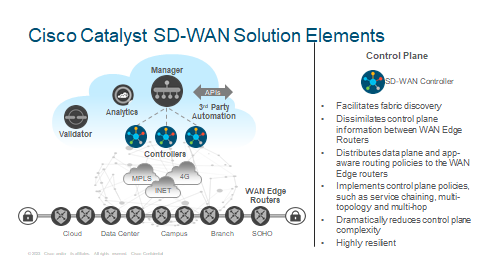
Controller
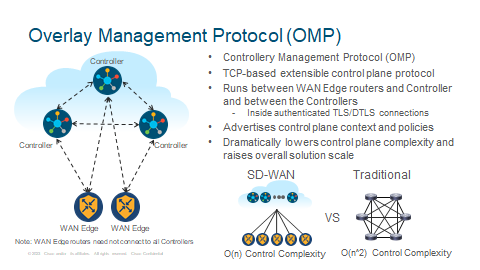
Cisco Controller are a scale-out control plane functions of the Cisco Catalyst SD-WAN fabric. Controller allows fabric discovery by running the Overlay Management Protocol, the OMP, between themselves and between themselves and the WAN Edges. Together with WAN Edges, Controller act as a distribution system which allows relevant information that is needed in order to establish data place connectivity beweeen WAN Edge to WAN Edge.
This information includes service side reachability, transport side IP addressing, IPSec encryption keys, site identifiers etc..
Control Policies acting on the control plane information are made locally on the Controllers and not the WAN Edge devices.
These control plane policies can implement service chaining, various types of topologies and dictate how the traffic will traverse.
A common similar comparison is the BGP Route Reflector in the traditional networking world. The Controller acts in a similar way except for the Control Policies will affect the Controllers.
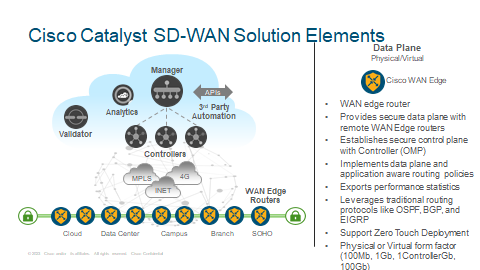
WAN Edge
Cisco WAN Edge routers are the data plane elements of the Cisco Catalyst SD-WAN fabric. They are in essence WAN edge routers positioned everywhere SD-WAN fabric needs to be extended to. WAN Edge routers are responsible for encrypting and decrypting application traffic between the sites. As mentioned earlier, WAN Edge routers establish control plane relationship with Controller to exchange pertinent information required to establish the fabric and learn centrally provisioned policies. Data plane and application aware routing policies are implemented on the WAN Edge routers.
WAN Edge routers leverage standards based OSPF, EIGRP and BGP routing protocols for learning reachability information from service side interfaces and for brownfield integration with non-SDWAN sites. For data plane redundancy, WAN Edge can be configured in L2 redundancy such as VRRP, even on a per-VLAN basis.
Zero touch deployment also can be utilised which relies on the use of signed certificates installed in the on-board temper proof module, the TPM) to establish unique router identity.
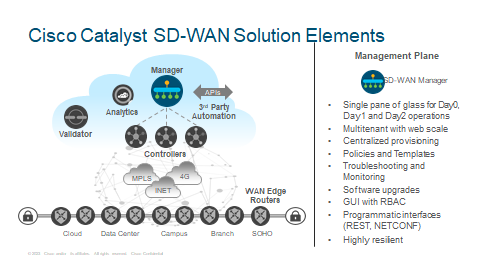
Manager
Cisco Manager provides single pane of glass for Day0, Day1 and Day2 operations. Its multitenant web-scale architecture that solves the needs of the enterprises and the service providers alike.
Some of it’s key functions include centralised provisioning, centralized policies and device configuration templates, ability to troubleshoot and monitor the entire environment and perform centralized software upgrades on all the fabric elements. Manager GUI allows segregated administrative access by implementing RBAC for proper roles and responsibilities. Performance statistics can be exported into external systems or to Cisco Analytics tool for further processing and deeper insight such as ThousandEyes WAN Insights (Sales Pitch!).
Fabric Operation
OMP is the routing protocol for SD-WAN, created by Cisco. It is essentially the same as BGP in how it works with the best path selection.
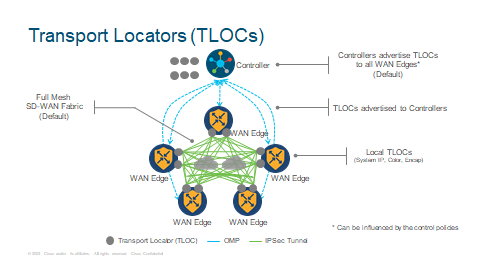
TLOCs
Cisco Catalyst SD-WAN can build secure overlay fabric on top of any public or private transport, such as MPLS, Internet, 4G LTE, Satellite, point-to-point circuits and so on. This gives the customer the flexibility without having to rely on one Service Provider and no matter which country you are in you do not need to purchase expensive backhauls. IPSec encryption is used for the secure overlay fabric. Transport locators or TLOCs, represent abstraction layer for defining IPSec tunnel endpoints. Cisco Catalyst SD-WAN fabric leverages [system IP, color, encapsulation] for defining IPSec tunnel termination endpoints. This allows independence from individual transport IP addressing.
TLOCs are advertised as TLOC routes in the OMP messages between the WAN Edge routers and the Controller. Controller reflect TLOC reachability between the WAN Edge routers across the fabric. In the absence of control policies on the controllers, all TLOC routes get advertised by the controllers to all WAN Edge routers. Control policies can be used to block certain TLOC route advertisements or modify their attributes before passing them along. Once advertised, WAN Edge routers can construct direct IPSec tunnels between themselves. By default WAN Edge routers construct a full mesh topology.
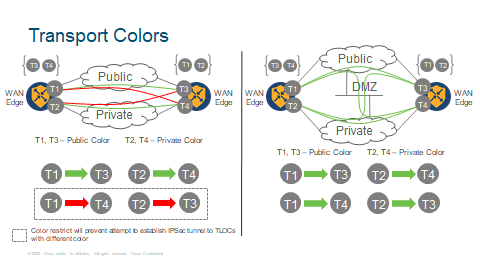
Colour
As color is one of TLOC attributes (along with system IP and encapsulation), Cisco Catalyst SD-WAN fabric allows creating a setup where WAN Edge routers do not attempt to establish secure IPSec tunnels with remote TLOCs having a different color than a local TLOC. This is called restrict option. With restrict, WAN Edge routers will not attempt building secure IPSec tunnels between private and public transports and as such, Manager will not report any downed connections.
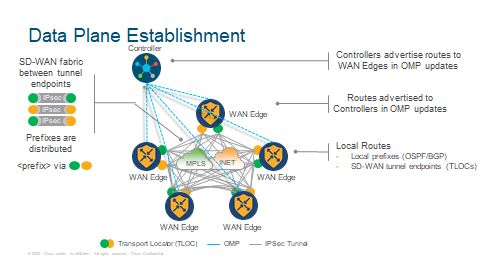
Data Plane Establishment
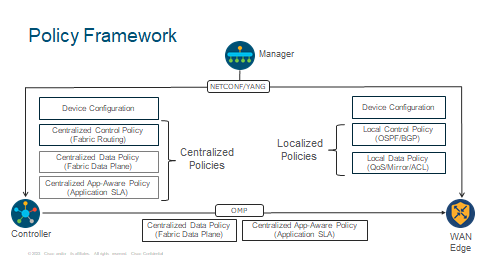
Policy Framework
This is a good example of where you would configure your policies and what will be affected. With Centralised Policies this is will be configured and sent to the the Controller. With Localised Policy, this will be done and affects the Data Plane (WAN Edge).
Data policies are primarily used to override fabric routing behavior with specific instructions in regard to next-hop, outbound transport, service insertion and so on. They can match on any of the 6-tuples (including DSCP value) in the TCP/IP headers or on one of the DPI signatures if it had been turned on. Application aware routing policies can enforce prevent application traffic of interest from being sent down the tunnels that do not satisfy the loss, latency or jitter SLA thresholds as defined by the administrator.
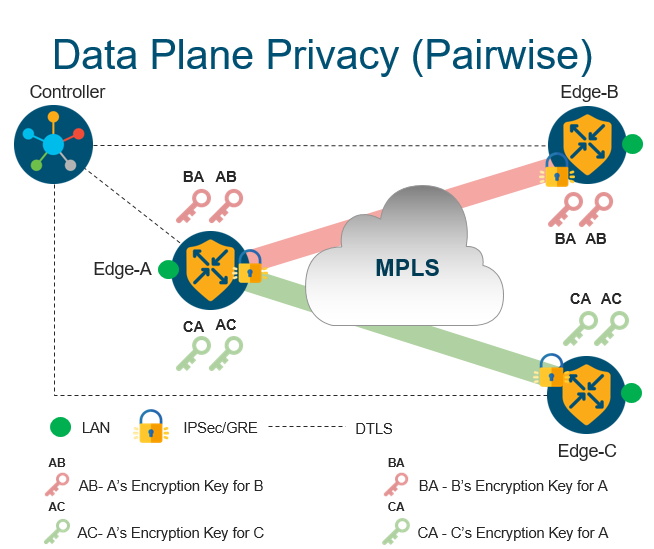
Data Plane Privacy
Each WAN edge will create separate session key for each transport and for each peer
Session keys will be advertised through Controller using OMP
When Edge-A needs to send traffic to Edge-B, it will use session key “AB” (B will use key “BA”)
Backward compatible with non PWK (PairWise Keys) devices
PWK should be enabled